RADIUS Overview
RADIUS(Remote Authentication Dial-In User Service) is a networking protocol, operating on ports 1812 and 1813, that provides centralized Authentication, Authorization, and Accounting (AAA or Triple-A) management for users who connect and use a network service.[1]
RADIUS is a client/server protocol that runs in the application layer. Network access servers, which control access to a network, usually contain a RADIUS client component that communicates with the RADIUS server. RADIUS is often the back-end of choice for 802.1X[2] authentication.[1]
WPA-Enterprise is also referred to as WPA-802.1X mode, and sometimes just WPA (as opposed to WPA-PSK), this is designed for enterprise networks and requires a RADIUS authentication server to have users can use a network service.[3]
The imRAD can be used on WPA, WPA2, and WPA3 Enterprise[3] environments and supports EAP-TTLS[4] and EAP-PEAP[5]. The EAP-TTLS is a default authentication method.
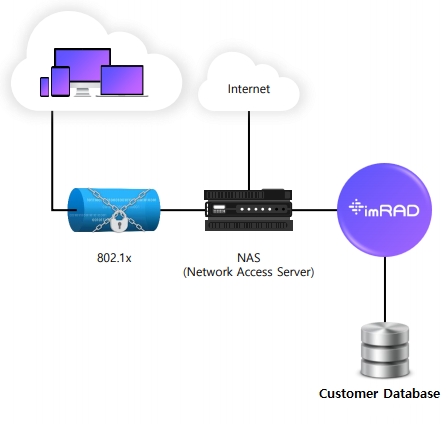
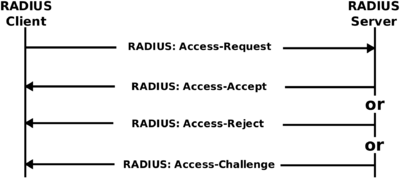
RADIUS authentication consists of supplicant(user device), NAS(Network Access Server), and the RADIUS server. The user or machine sends a request to a Network Access Server (NAS) to gain access to a particular network resource using access credentials. The NAS sends a RADIUS Access-Request message to the RADIUS server, requesting authorization to grant access via the RADIUS protocol. The RADIUS server checks that the information is correct.
The imRAD was developed based on the FreeRADIUS and provides the most of RADIUS services. Our system can authenticate a User-Name in a Local database, remote databases, or LDAP servers, and Proxy servers. The following is the supporting remote DBMS or LDAP.
- MariaDB
- MySql
- Oracle 11g ~ 19c
- Microsoft SQL Server 2014 ~ 2019
- Tibero 6
- PostgreSQL 12
- SYBASE
- OpenLDAP
- Microsoft Active Directory Domain service(AD DS)
- Microsoft Active Directory Lightweight directory service(AD LDS)
Using an external Database makes it possible to authenticate directly a user through it(e.g, Customer employee database) without importing data from the remote database to the imRAD local database.
In the environment of user authentication via an external Database, it may increase network traffic to the external database and slow down the database.
To resolve this, the user credentials that were authenticated from an external database are saved into the local database for few days(You can set how many days the cached users are kept in the local database from the RADIUS general settings). And then, authentication requests will not be sent to the external database but be completed in the local database. We called it "cached user".
To securely save the User-password into the local database, it is saved as hashed data using the strong hash algorithm(e.g, SHA256 with salt).
Supporting TLS(Transport Layer Security) version is between 1.0 and 1.3 and can be changed the minimum and the maximum version from the RADIUS general settings. You must make sure the TLS version because some client operating systems still use TLS 1.0.
RADIUS Proxying is that the server can proxy any request to other RADIUS servers and other RADIUS servers can authenticate the proxying request.[6] A famous proxying is eduroam(education roaming)[7] and a user can be authenticated at an eduroam server using the RADIUS Proxying.
An external database authentication and a RADIUS Proxying can be restricted by a NAS Identifier(NAS-ID) and you can also set this policy on RADIUS> Settings> Authentication DB or Realms/Proxys menu.
Configuring RADIUS
Getting started
Basically, to authenticate a user's device that is in the 802.1x environment, Follow the below instruction.
- Register the IP address of an imRAD N1 and the shared secret at a NAS.
- Register the IP address of a NAS and the same shared secret at the RADIUS > settings > NAS .
After doing the above, the imRAD RADIUS can process the requests from the NAS that was registered. If you want to test a device(e.g, smartphone, tablet, laptop computer, and so on), please refer to the RADIUS Authentication testing.
Users
It manages 802.1x Users.
Reject2ban
It is designed to reduce the load on the databases from random requests of a malicious client.
Groups
It is the RADIUS User groups.
Attributes
It provides a manager can search the attributes used in RADIUS.
Log
- Accounting: It displays all Accounting.
- Post-Authentication: It displays all log after attempting authentication.
- Reject2ban: It displays the Reject2ban log.
Settings
All settings for the RADIUS can be configured on this menu. After configuring something, the radiusd service will automatically apply the changed values in few seconds without an administrator manually restart the radiusd service. If you want to radiusd service can forcibly apply the changed value, click the "Apply" button at the bottom of this menu.
General
You can configure Data Maintenance, Password complexity for RADIUS User-Password, EAP, RADIUS general configuration, and Reject2ban.
NAS
As a feature for managing the Network Access Server, you can add or remove wireless LAN controllers or Access Points (APs).
Realm/Proxy
It manages Proxy servers and Realm for the Proxy Authentication.
Authentication DB
Configure local or external database connection attributes for user authentication.
LDAP
Configure LDAP(Lightweight Directory Access Protocol) or AD(Active Directory) server connection attributes for user authentication.
NAS-ID
It manages automatically collected NAS-ID (SSID).
Captive portal
This is an interface that allows you to create pages for wireless LAN usage instructions and wireless LAN user registration when using Captive Portal.[8]
RADIUS Authentication testing
It shows several EAP methods for operating system-specific authentication tests.
References
- ↑ 1.0 1.1 1.2 https://en.wikipedia.org/wiki/RADIUS
- ↑ https://en.wikipedia.org/wiki/IEEE_802.1X
- ↑ 3.0 3.1 https://en.wikipedia.org/wiki/Wi-Fi_Protected_Access#WPA2
- ↑ https://en.wikipedia.org/wiki/Extensible_Authentication_Protocol#EAP_Tunneled_Transport_Layer_Security_(EAP-TTLS)
- ↑ https://en.wikipedia.org/wiki/Protected_Extensible_Authentication_Protocol
- ↑ https://wiki.freeradius.org/features/Proxy
- ↑ https://www.eduroam.org/what-is-eduroam/
- ↑ https://en.wikipedia.org/wiki/Captive_portal