Overview
Reject2ban is a feature that denies authentication for a certain period (bantime) to a client (supplicant) if the client experiences authentication failures exceeding a specified threshold (maxretry) within a designated time window (findtime). Clients denied authentication with this configured timeframe are registered in the Reject2ban Jail. After the time registered in the Jail elapses, the banti me must pass before the client can request authentication again.
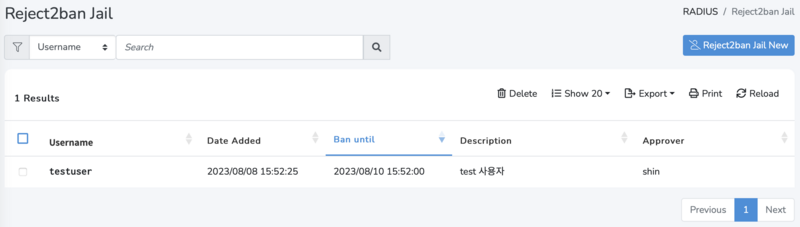
Reject2ban Jail
The RADIUS > Reject2ban Jail menu displays users jailed by the Reject2ban criteria and automatically removes them from the list when their bantime expires. However, due to a 10-minute interval for automatic removal checks, the exact match with bantime might not occur.
Even if a user is included in the Jail, if their release time is less than the current time, their authentication requests are processed normally.
When a user's name is included in the Jail, their authentication requests receive an Access-Reject response without querying the authentication database (local and external). This prevents overloading the authentication database from attacks like brute-force. For instance, with a findtime of 10 minutes, maxretry of 100, and bantime of 5 minutes, if 100 Access-Rejects occur within 10 minutes, the client is registered in the Jail, and authentication is denied for 5 minutes without executing any database queries.
However, note that depending on the configuration of a wireless controller or and Access point, more requests from clients may reach the authentication server than the authentication request count, so setting sufficient values is recommended. In other words, due to possible retransmissions by the wireless controller, even though a client makes one request, the authentication server might receive more than two authentication requests, considering them as two authentication failures.
Furthermore, if a client attempts authentication during the bantime period after being jailed, no authentication failure feedback is sent to the client. Therefore, user notification is necessary.
To immediately allow authentication again for a jailed client, you can delete the client from the Reject2ban Jail menu.
• Ban Added: Indicates the time when the client was added to the Jail.
• Ban Until: Indicates the time the client will be removed from the Jail; it's "Ban Added Time + bantime" for automatic registrations and the time set during manual registration for manually added clients.
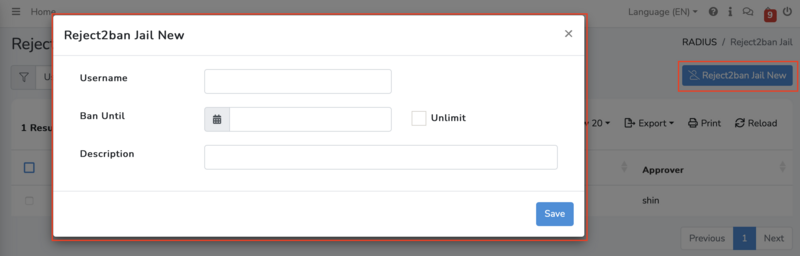
Manual Registration
You can manually register a new user into the Reject2ban Jail by setting the "Username" and the "Ban Until" from the Jail.
Reject2ban Setting
You can configure bantime, findtime, and maxretry in RADIUS > Setting > General > Reject2ban. Initially, this feature is disabled, so change it to "Enabled" if desired, and set the other values. Recommended values are 120 minutes for bantime, 60 minutes for findtime, and 60 for maxretry.
This feature aims to reduce database load from abnormal requests of some malicious clients. Setting values lower than recommended might unintentionally include legitimate clients in the Jail and deny authentication.
Reject2ban Log
RADIUS > Log > Reject2ban includes the history of users who were registered in the Reject2ban Jail due to meeting the Reject2ban criteria (findtime, maxretry) and were subsequently released after bantime. It also includes records of manual additions or exclusions by administrators.